Canon MJ Delivered Security Information Cyber Security Information Bureau ESET Is that virus warning?What is the meaning of the warning display issued by the iPhone?
Security mechanism to ensure the iPhone
Compared to Android smartphones (hereinafter, smartphones), the public is generally recognized that security is robust.To support the image, the iPhone has taken strict security measures.The following are three security measures implemented by the iPhone.
iOS "Sandbox"
The iPhone has introduced a "sandbox" mechanism in the execution environment of the app.A sandbox means "sandbox in the park", but it is a good idea to imagine a wall -like wall that is surrounded by a net.Executing the app in the sandbox does not affect the area of the sandbox even if dangerous occurs.In short, apps executed in an isolated environment inside the iPhone do not affect other apps and OS itself.As a result, the app cannot be performed by Trojan and worms, such as the application communication with other apps or growing apps.
Examination on the official app store "App Store"
To distribute apps to install on the iPhone, you need to be screened at the App Store.In the screening, the safety is ensured by checking items such as unauthorized acquisition of user data and adding inappropriate metadata aimed at the optimization of search in the App Store.Bug identification, private API checking, etc. are also performed.
Limited to download via "App Store"
Basically, the apps that can be installed on the iPhone are limited to downloaded on the App Store.What is distributed in the App Store has passed the screening as described above, so that a certain level of safety is guaranteed.Also, iOS14.After 5, privacy requirements have been stricter, and the level of security has been improved.
For example, regarding user tracking, third -party cookies were used to be used, but now to access users' behavioral tracking and user device advertising, users are used through the App Tracking Transparency framework.You need to get permission.
Also, it is difficult for users to understand that the apps that have been installed in the past have performed suspicious behavior.iOS14.In the past, even if the permission of the user in the past, if the risk is assumed, the alerts are increased, so safety is increasing.However, it is important to guarantee that security is when you are using a "general" iPhone, and that it is not the so -called "jailbreak".I need it.
What is the security display made by the iPhone?
When using the iPhone, the following is a case where a user emits a security alert when a user reaches a high security risk.
"Warning of fraud website"
This warning is issued when accessing the website, which is suspected of fraud on personal information, including credit card numbers.For example, there is a case where a notification of a courier service is sent via SMS, and if you click the link in the notification, such a warning will be displayed.This kind of warning is displayed when accessing a website where phishing fraud is suspected, so you should refrain from accessing the site if it is displayed.
"Recommendations for key chains"
A key chain is a password management function using iCloud.It is highly convenient and many users are using it.When entering a password using this key chain, you may encourage users to change the password.In that case, a text such as "This password has been detected by data leakage" is displayed in the change notification.
If this warning is issued, the password is likely to be leaked, so I would like to change the applicable password promptly.Also, if you are using a password, don't forget to change your password for other websites and services.
"Low security"
A warning issued when using an old standard encryption method such as WEP and WPA2 when connecting to Wi-Fi.Connecting does not always encounter damage, but more risk is higher than the latest WPA3.Especially in the WEP method, even the recent processing capacity of the recent PC is deciphered in less than a few minutes.If you use it as a Wi-Fi at home, it is recommended that you replace it with a new standard as soon as possible.If it is a recently released router, most of the Wi-Fi6 standards are compatible with WPA3.
Wi-Fi6は安全かつ高速なネットワーク接続を実現する?In addition, the public Wi-Fi can be used as much as possible and connects to the Internet via VPN when using it, enhancing safety.
"Do you trust this computer?"
When backing up the contents of the iPhone to the computer, this message is displayed at the first connection.By selecting "Yes", you can access your iPhone data from your computer.Therefore, do not allow unreliable PCs.It was revised in the OS update in November 2020, but iOS has also discovered vulnerabilities in the past that attackers could abuse trust and download malicious content.
In addition to those introduced so far, various alerts are emitted on the iPhone.I want to check the contents of the alerts each time, not the reason for the troublesome or troublesome reason.
Fake security warning "Fake Alert"
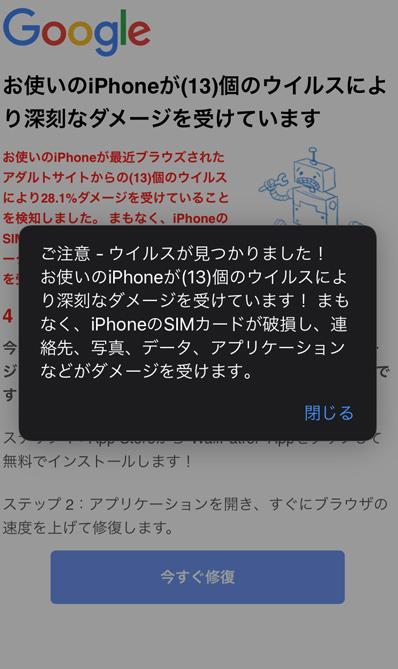
As we have seen so far, iPhone security measures have been strengthened.As a result, many users use it under the perception that security risks do not occur.Be careful of fake alerts, an attack method that takes such a psychological state on the other hand.Fake alert is simply a "fake warning message".Mainly, it is often emitted while browsing the website with a browser, and as shown in Fig. 1, it threatens the user as if it were severely damaged, despite being infected with the virus.
Fig. 1: Examples of fake alerts emitted during browsing in Safari
Even more malicious is that if this page is displayed, just tapping the "return" button on the Web browser cannot return to the original page.As a mechanism, the method of redirect on the website is used.By preparing multiple redirect, the redirect will continue even if the user taps the "return" button over and over.
Attackers are aiming to click on the "repair now" displayed on the screen so that users who cannot return to the original page forever are tapped.In fact, tapping the "Repair now" button is guided to a page that sells suspicious restoration apps.Of course, it goes without saying that there is no point in buying this app because it is not infected with malware.
In such a situation, the most appropriate way to deal with the tab from the "tab" button of the web browser.In the case of Safari on the iPhone, tap the tab icon where the □ in the lower right is overlapped and tap the “×” displayed at the upper left of the closing tab.Many fake alert pages are simple web pages as a mechanism, so if you erase the page itself, there is no danger.
However, it is hard to imagine that such fake alerts will change their hands and generate them.As a user, we want to eliminate the risk of damage by calmly dealing with this situation.
Vulnerability and correspondence of the iPhone
There is a risk of vulnerabilities even for iPhone, which is said to be highly safe.We will introduce specific vulnerabilities and countermeasures.
Jailbreak (Jail Break)
Apple, an iPhone provider, is known for its severe security requirements in app development.Although such attitudes were successful and boasted robust security, in the past, the strictness restricted the function of the app.As a result, the OS has been remodeled so that some users can install apps without going through the App Store.This act is called "jailbreak".By jailbreak, you can usually prohibit prohibited.
However, if you jailbreak and use an unchecked app, the risk of malware infection will increase dramatically.In addition, since the operation may be unstable, the iPhone with jailbreak history is not supported, so even if a failure occurs, it cannot be repaired.Recently, the iPhone's functional extension has progressed, and the merit of jailbreak has been reduced, and easy jailbreak is not recommended, taking into account the risks associated with exchange.
Zero Day attack
A zero -day attack is an attack that hits the vulnerabilities that have not been recognized in the past.Although people involved in the development of the iPhone are stuck in finding vulnerabilities every day, it may still be a characteristic of programs that intermittent vulnerabilities are discovered.In the case of high -risk vulnerability on the iPhone side, or if the zero -day vulnerability is found to have been used for attacks, OS and application fixing patches are promptly distributed.
As a user, I would like to make sure that the "automatic update" of "Software Update" is turned on in the iOS "settings".Also, if an update is distributed on the App Store for the app, it is better to make it quickly applied.
Supply chain attack
There are two supply chain attacks: entering corporate trends and those that enter the development process of software and apps.The latter supply chain attack is affected by the iPhone, which is a process that is used in software used as a development environment, and is eventually incorporated into the completed software.The official app is checked for suspicious actions at the time of registration on the App Store, but there is also a type of malware that hides without suspicious behavior at the time of screening.
Users recognize that they are not stones just because they have passed the App Store screening, and delete suspicious and unnecessary apps as appropriate.
Zero click?New threat to iPhone
As a result of smartphones indispensable for everyday life, the number of attacks aiming at smartphones is increasing year by year.And the risk is not unrelated to the iPhone.The fact is that there is no way to defend the clever attack method, such as the zero day attack and the supply chain attack.
Recently, the existence of spyware called "Pegasus" has become a hot topic in the security industry.This spyware is iOS14.It is said to be malicious, such as infection with the iPhone below 6, secretly transferring messages and photos stored in the terminal, or recording calls.
The infection method is also troublesome, and by sending a specific "message" data to the targeted iPhone, the OS is abnormal, and the OS itself downloads and launches malware.It is thought that the so -called zero click vulnerabilities were exploited and installed.
Although the vulnerability that PEGASUS has already abused has been taken in the latest version of the OS, but it is undeniable that the appearance of the variants has become a big deal.After all, the user is required to take measures as needed and take measures as needed.
For example, in driving a car, even in the case of an iPhone, it will confront various risks in its use, as it is always next to some kind of risk.As a user, we want you to catch up your daily attack methods and related risks, and constantly take appropriate measures to protect yourself.