Security information for safe digital use provided by Canon MJ Understand the mechanism of ESET sandbox, cyber security information office, and increase the safety of your computer
How does the sandbox work?
A sandbox is a mechanism that runs a program in an isolated area so that it does not affect other programs even when a problem occurs. In Japanese translation, it means "sandbox" in a park, and comes from the situation where people can play freely in an environment that is partitioned off from the outside.
Figure 1: File verification mechanism using sandbox
The advantage of running a program in a sandbox is that even if it is a malicious program, you can check its behavior in an environment that does not affect external programs. Protect areas outside the sandbox by restricting access by programs running in the sandbox when they do not have explicit permission to read or write files, access the microphone or camera, etc.
A typical example is analyzing incoming emails in a sandbox and detecting malware. In the sandbox, attachments and links in emails can be verified, and some systems can even notify users if they contain problematic programs.
Figure 2: Mechanism for verifying incoming emails in a sandbox in a virtual environment
It is difficult to detect sophisticated attacks such as targeted attacks and zero-day attacks, which have been increasing in recent years, using the conventional pattern matching method that compares them with known programs. However, the use of sandboxes improves the detectability of these attacks by running real, externally injected programs in an isolated environment.
Many other applications also employ sandboxing mechanisms that may run unknown programs. For example, web browsers run programs such as JavaScript in an isolated area, and give explicit permission to use things like the camera. In addition, plug-ins such as Adobe Flash also have a sandbox that restricts file reading and writing on the device.
On mobile devices, operating systems such as iOS and Android are designed to run apps in a sandbox. Even apps downloaded from the official app store, apps developed by third parties may contain bugs, which is a security risk. The idea is to protect the risk on the OS side.
Are sandbox iPhones immune to malware? What measures are really necessary?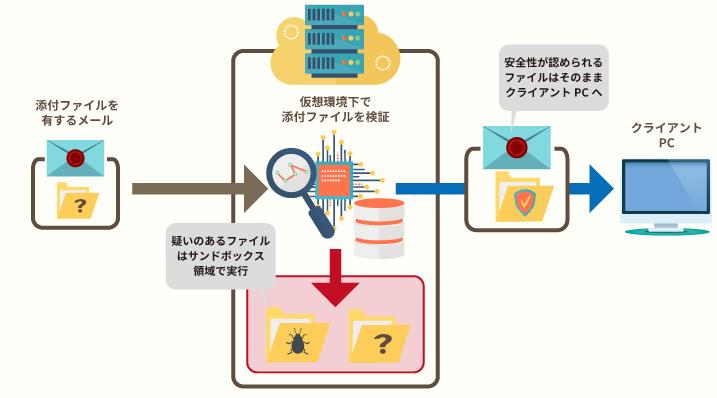
Challenges and countermeasures for using sandboxes against malware
As mentioned above, sandboxes are used as countermeasures against malware, but security issues have also been pointed out. First, it takes a certain amount of time to analyze whether it is malware in the sandbox and complete it. Therefore, it is difficult to respond in real time. For example, when inspecting received e-mail, the e-mail may have already reached the recipient by the time malware is detected.
Some malware detects whether it is running in a sandbox environment and bypasses countermeasure software. Since there are unique MAC addresses and processes in virtual environments such as VMWare, it detects the status of execution in the virtual environment and temporarily stops its behavior as malware. The theory is that by resuming activity after passing through countermeasure software, the probability of a successful attack is increased.
There are also malware programs that are scheduled to run at specific times. In this case, the sandbox cannot detect malicious behavior outside of the specified time, so there is a possibility that the program will be breached as an innocent program.
In fact, the crypto-ransomware Locky is well known for its ability to bypass sandboxes. Spam emails and vulnerabilities in Flash were used to infect many computers. Once infected with Locky, the files on your computer will be illegally encrypted and you will be blackmailed to pay for the decryption. Locky is a ransomware that spread around 2016 and 2017, and damage was reported all over the world, including Japan.
Additionally, malware that runs in memory without using files has been discovered. Even in this case, the file cannot be executed in a sandbox environment, so there is a high possibility that detection can be evaded.
Considering that there is a wide variety of malware as described above, it is not desirable to rely solely on sandboxes to improve security. It is important to have a multi-layered defense perspective, in which multiple measures are taken at different levels. In many cases, the terminal side is targeted, so in addition to detection on the server side, security measures at the endpoint are also essential.
There is also a mechanism called a honeypot as a technology related to the sandbox. A honeypot is a fake system that is set up with the purpose of launching an attack, and is used to lure attackers in order to observe and investigate their methods and behavior. It is more likely that systems with vulnerabilities are targeted than actual servers, and is said to have the effect of improving security. Although the idea is different from sandbox, it can be said that it is common in that it uses an environment separated from the actual system to protect itself.
HoneypotSandbox-type virtual environment with expanding possibilities
The sandbox concept is not limited to email countermeasures and mobile operating systems, and is being applied in a variety of situations. For example, when running virtual machines, the sandbox idea has been applied to prevent interference between the host computer and virtual machines. Sandboxes are also used when building a specific environment in software development and executing tests.
Docker is widely used as a container technology for building a virtual environment. Virtual environments such as VirtualBox and VMWare have also been used frequently. Recently, a tool called Windows sandbox has come to be provided in the Windows environment. It has the advantage of being able to run files in the Windows sandbox without affecting the environment you use on a daily basis, such as checking the behavior of programs developed by third parties or conducting software development tests.
An open source software called cuckoo is known as an anti-malware tool that uses a sandbox. You can run a program in a virtual environment, and record the started processes, read/write of files, and IP addresses of communication.
Similarly, ESET Dynamic Threat Defense is a cloud service that leverages sandboxing to increase defense against unknown malware. Suspicious files found on the terminal are automatically sent to a sandbox environment on the cloud, and after verifying their behavior, malicious programs are immediately blocked. Threat information is constantly updated on the cloud, so even zero-day attacks can be dealt with immediately, which is a major advantage.
Sandboxes used out of sight of users, such as web browsers and mobile apps. In recent years, it has become possible to build a wider range of sandbox environments, not limited to enterprise products. That's why I want you to properly understand the concept of sandboxes and use them to help you use your computer and the Internet safely.